Please note: This article only applies to standalone customers. This article does not apply to those who are integrated into the broader Paycor HCM platform.
SAML 2.0 with Microsoft AD FS
This section will outline the specific steps needed to setup SAML 2.0 SSO with Microsoft Active Directory Federation Service (AD FS) 2.0.
Note: We officially only support Microsoft AD FS 2.0. It should be possible to use AD FS 3.0 (also know as ADFS 2012 R2) using instructions outlined here.
Tip: These instructions apply to SSO only; you'll still need to manually provision and deprovision accounts in 7Geese.
Obtain your Federation URL
You should be able to obtain your federation url from the Certificates section of ADFS 2.0 by looking for the CN name. If you are unsure, please ask your system administrator.
Under Token-signing, right-click on CN=ADFS and click View certificate..
From the Details tab, ensure Show is set to All. Click Copy to File...
You'll then be taken to the Certificate Export Wizard. Click Next.
From Export File Format, under Select the format you want to use, select Base-64 encoded X.509 (.CER)
You will need to convert your certificate from DER to PEM. You can use this online tool: https://www.sslshopper.com/ssl-converter.html
Setup 7Geese
You can setup a new SAML connection by adding a new SAML integration from the integrations section in your organizational settings: https://app.7geese.com/admin/integrations/
Fill out the following fields for the SAML integration with the corresponding values. Replace adfs.7geese.comwith your own AD FS domain that you found in step 1.
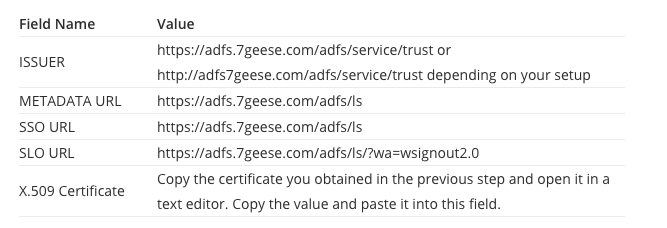
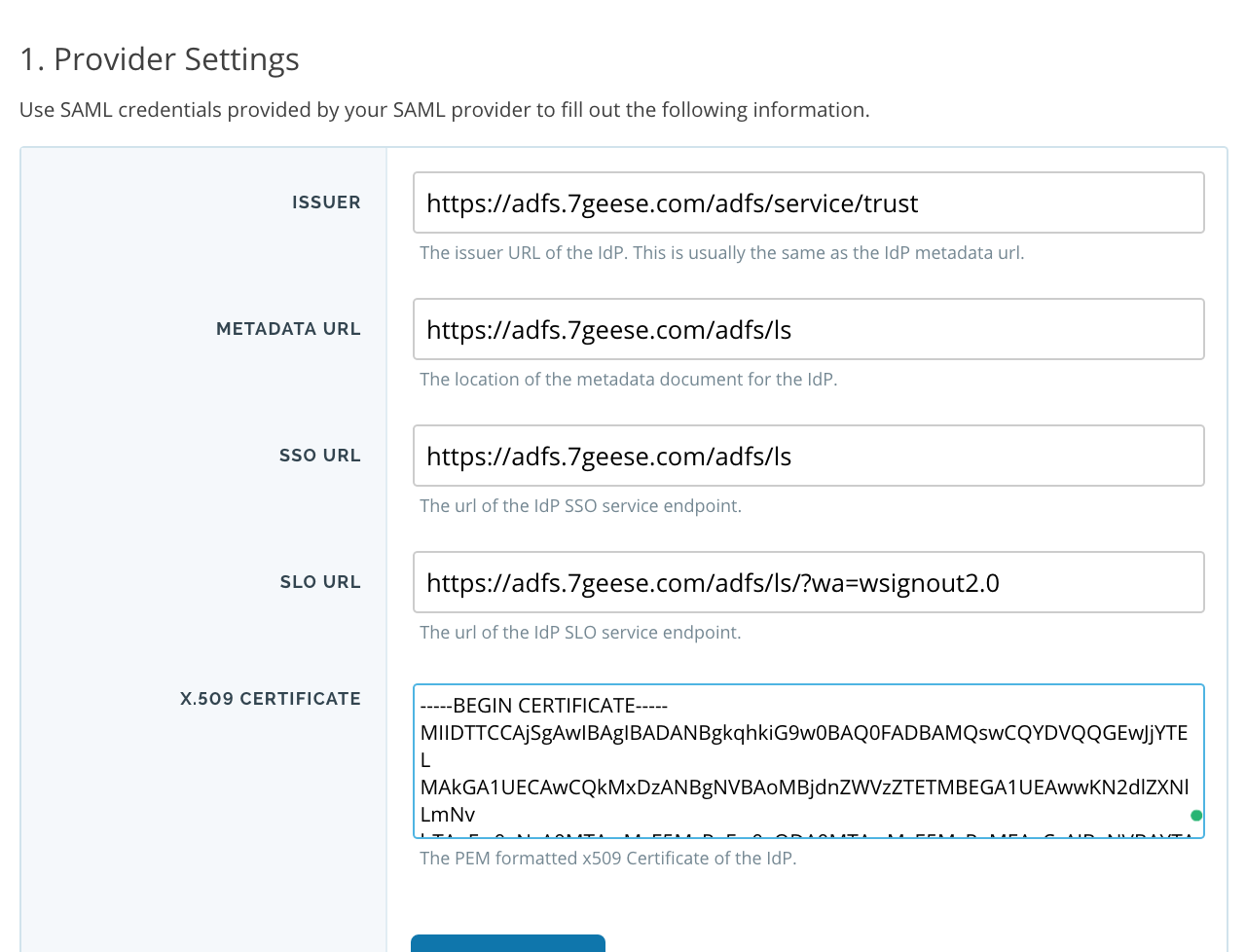
Once you are done, click Save settings.
You should now see a SAML Config area on the page. Make a note of all the fields on this page. We will use it in the next steps.
Configure Microsoft AD FS 2.0
In the AD FS 2.0 Console, under Actions, select Add Relying Party Trust....
Press Start.
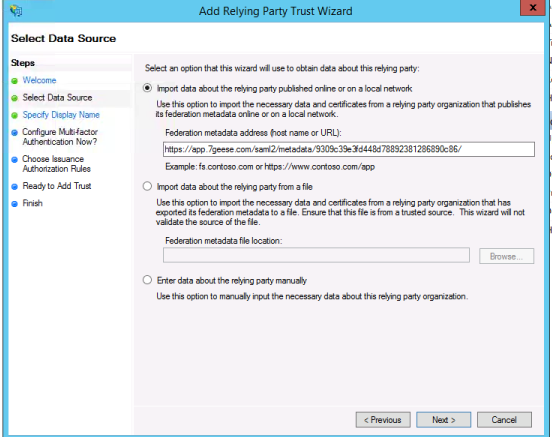
Choose Import data about the relying party published online or on a local network. Paste the Issuer URL that you noted down earlier from the SAML Config section. Click Next.
Choose a display name. You can leave it the default or type in a more descriptive name. Click Next.
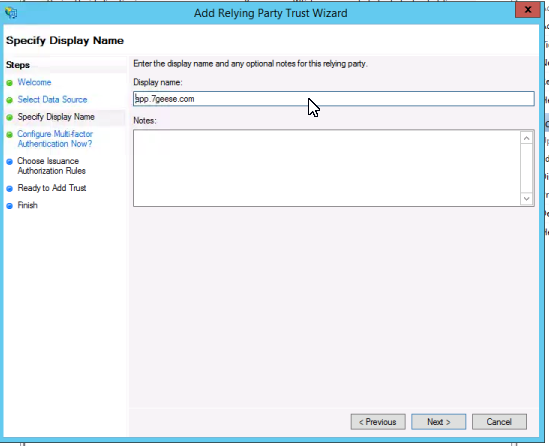
Pick I do not want to configure multi-factor authentication settings for this relying party trust at this time and click Next.
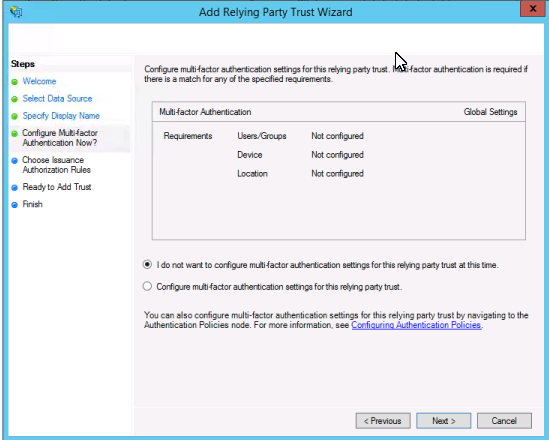
Pick Permit All users to access the relying party and click Next.
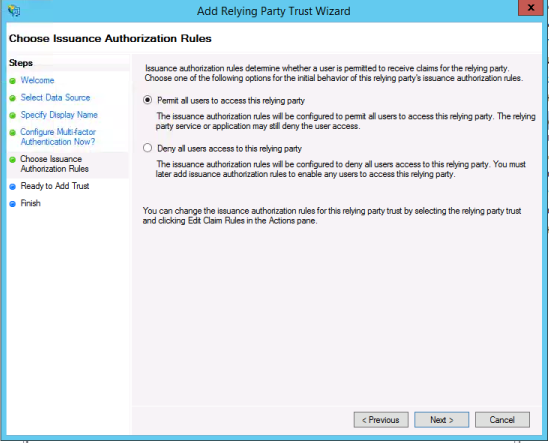
Click Next for the Ready to Add Trust section and then Finish.
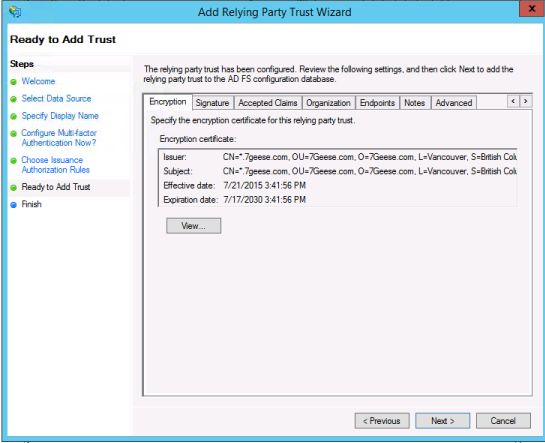
Right click the new Relying Party Trusts and choose Edit Claim Rules. Click Add Rule.
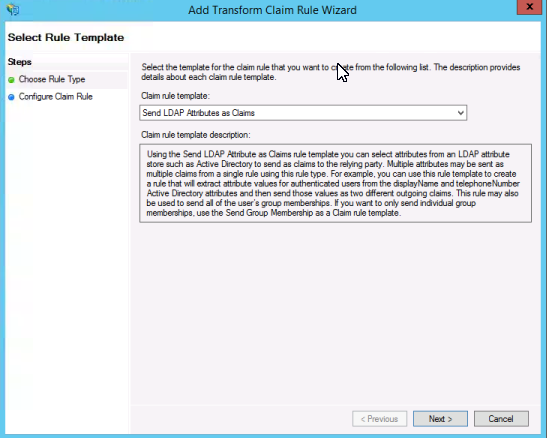
For the Claim rule template pick Send LDAP Attributes as Claims. Click Next.
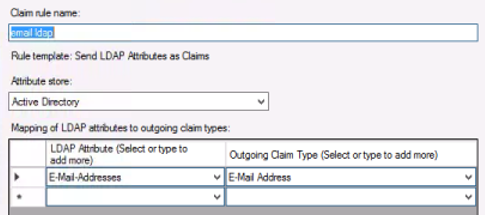
Pick a name for the claim rule such as LDAP Claim. In the drop down for Attribute Store choose Active Directory. Choose E-mail-Addresses on the left dropdown under LDAP Attribute column and choose E-mail Address under the Outgoing Claim Type. Then click Finish.
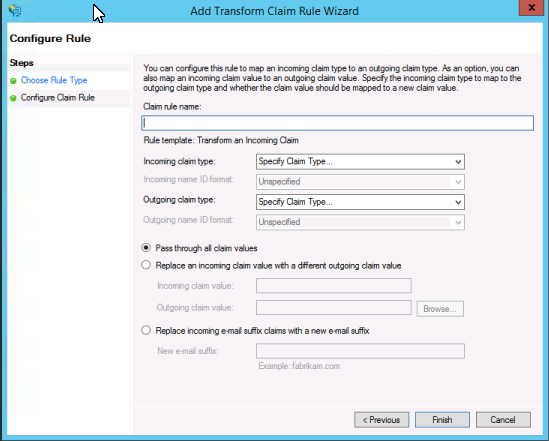
Add a new rule and choose Transform an Incoming Claim for the Claim rule template. Click Next.
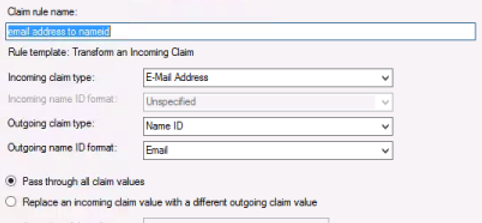
Pick a rule name like email address to nameid. Pick E-mail Address for Incoming claim type . Pick Name ID for Outgoing claim type. For Outgoing name ID format choose Email. Keep pass through all claim values checked and click Finish.
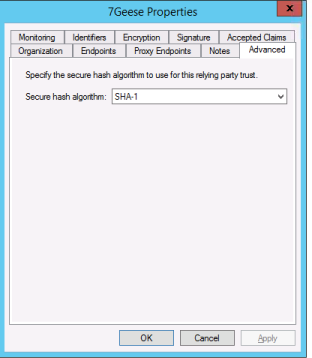
Right click relying party trust that we created and choose Properties. Click advanced and make sure the selected Secure hash algorithm is SHA-1. Click Ok to save your settings.
Final Steps
You're all done. The integration should be setup successfully. Use the test link provided in 7Geese to test the integration before you activate it.
